CyberVor May Have Stolen 2 Million Passwords
- Published in Security
On the heals of the good news about CryptoLocker decryption keys being found, here's some bad news about another cyber crime group out of Russia called CyberVor who has stolen what is believed to be the largest number of online credentials to date.
The name CyberVor is not as strange as it seems, as vor is simply Russian for thief. This is not a name they've given themselves, but rather then name given to them by the company that discovered their actions.
It is believed that CyberVor has successfully stolen 1.2 billion usernames and passwords, along with 542 million email addressees from over 400,000 different websites. That is a nearly unbelievable amount of data.
The information comes to us from Milwaukee company Hold Security who has used DefCon in Las Vegas to announce their discovery of the theft. As a part of the announcement Hold Security is also promoting it's identity monitoring services.
Hold Security has said, "Hackers did not just target US companies, they targeted any website they could get, ranging from Fortune 500 companies to very small websites. And most of these sites are still vulnerable." The reason they are still vulnerable per Hold Security is CyberVor used botnets to identify websites with SQL injection vulnerabilities to acquire the data. In layman's terms they used a flaw in the way certain websites are programmed to gain access to the data.
One of the concerns with this discovery, as outlined by Graham Cluley's blog "Security firm that revealed 'billion password' breach demands $120 before it will say if you're a victim", is that Hold Security is not offering up much detail on the discovery. Hold Security has not provided information on which sites it's determined where victims of the attack and thereby what online users should be concerned, nor have they provided details about a timeline, other than it was a 7 month investigation.
As an alternative to providing Hold Security $120 and your passwords, which no IT professional I've ever met would recommend, go to HaveIBeenPwned to find out if your account has been part of one of any large data breaches. Below is an image of what information a breached account will receive. 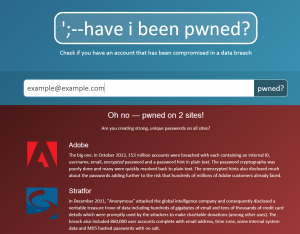 In the end I have to say we all at Top Speed agree with Graham Cluley, there is something not right about this kind of a major disclosure with so little real facts being provided and the only way to find out if you're a victim costs you both money and submitting your passwords.
In the end I have to say we all at Top Speed agree with Graham Cluley, there is something not right about this kind of a major disclosure with so little real facts being provided and the only way to find out if you're a victim costs you both money and submitting your passwords.
A couple of fake websites setup to look like Hold Security's password and email submission page and people will just be victimized all over again...


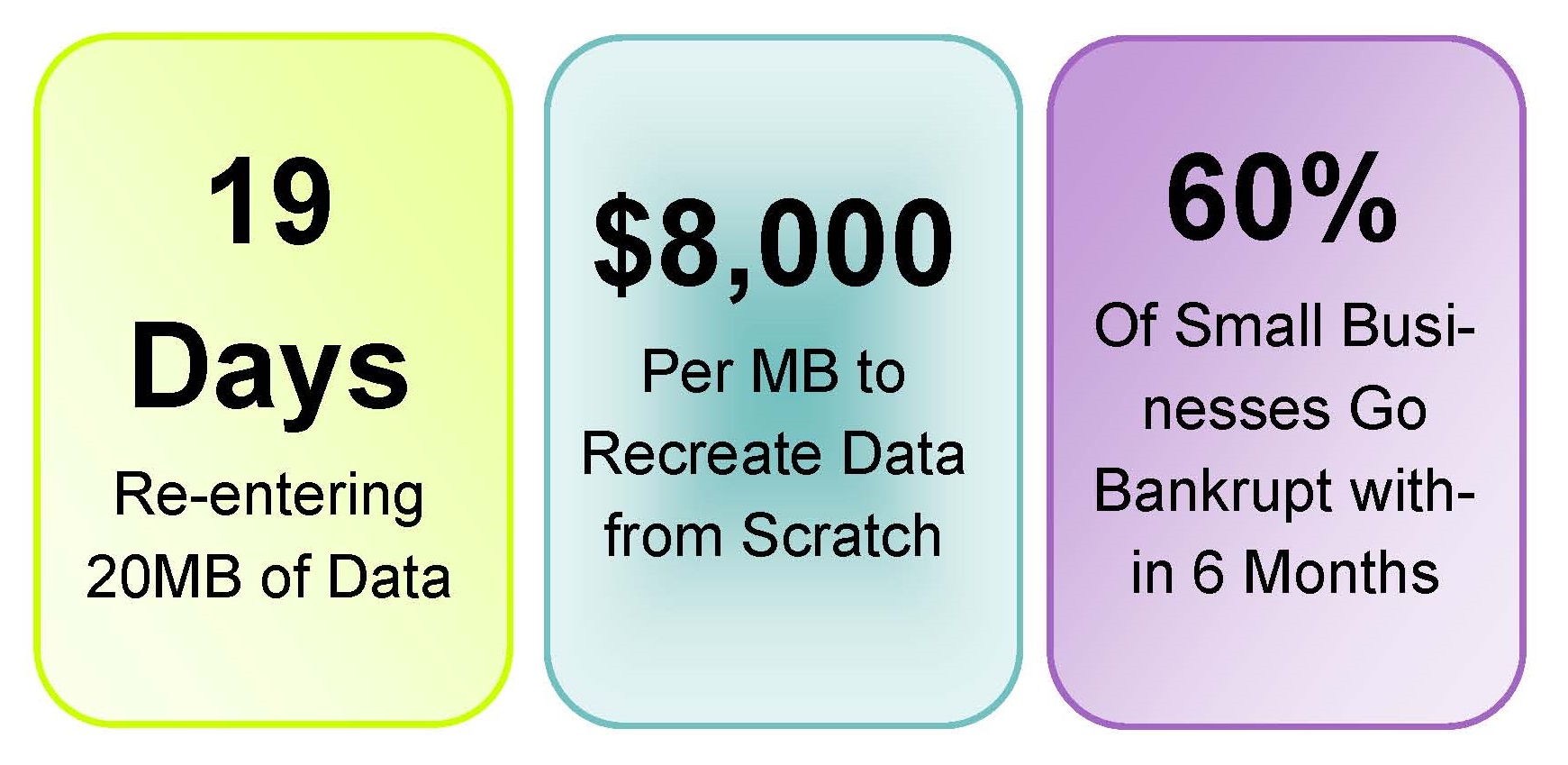

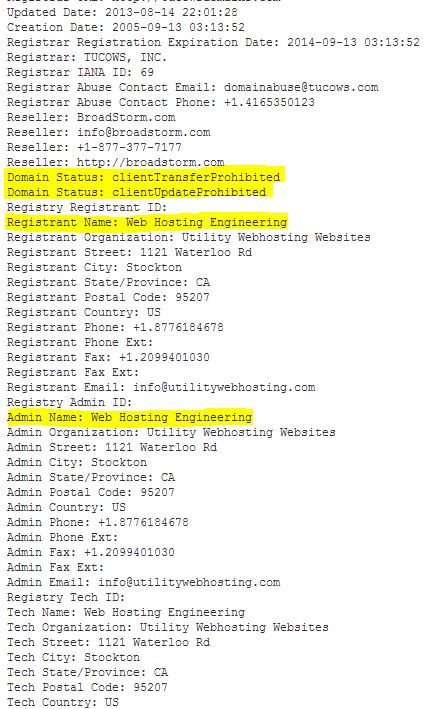
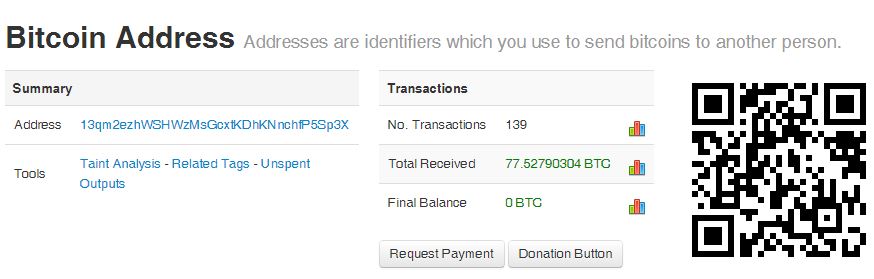
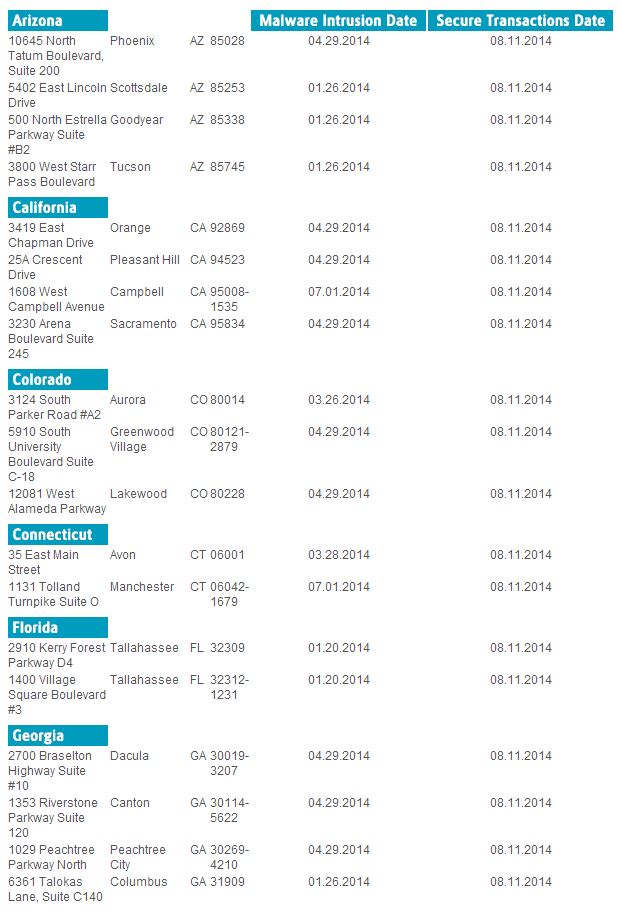

 PastaLeads is one of the most annoying Adware out there. This isn't the kind of infection that just slows down your computer, this nasty piece of Adware creates a Windows service that constantly runs in the background and as if that weren't bad enough if also configures your web browser to use a proxy server.
PastaLeads is one of the most annoying Adware out there. This isn't the kind of infection that just slows down your computer, this nasty piece of Adware creates a Windows service that constantly runs in the background and as if that weren't bad enough if also configures your web browser to use a proxy server.